The following overview covers some of the prolific trends which illustrate the scope of digital authoritarianism and information controls in Azerbaijan observed and documented in the past year.
Introduction
This report covers the online attacks targeting personal information and devices of human rights defenders, activists, and democracy advocates in 2022. The data is collected through media monitoring and information that was made available by targeted individuals who received support and assistance in mitigating the targeting.
Overall, 2022 has been no different than recent years in terms of online attacks and internet censorship observed in Azerbaijan. Activists, human rights defenders, and democracy advocates received phishing attacks and were summoned to law-enforcement bodies for criticism voiced online where their personal data and devices were often interfered with in the absence of the owner’s consent.
In some cases, there were reported hacking attempts and installed spyware programs. In January – December 2022, we observed overall 10 such cases.
Hacking and phishing attacks usually targeted the social media and email accounts of targeted community members. These were possible through the interception of SMS messages (set up as 2FA). In fact, SMS interception has been the main practice, leading to the hacking of scores of personal accounts, the paralyzation of social media accounts, the deletion of online posts, and the dissemination of personal information belonging to the targets.
Among some of the prominent cases was political activist Bakhtiyar Hajiyev whose social media accounts were targeted on multiple accounts. Hajiyev was also kidnapped twice in April and August 2022 and he was taken to the law-enforcement bodies. Police gained access to his social media accounts by force and removed posts that were critical of the authorities and state institutions. Hajiyev was arrested on December 9, on bogus charges, and sentenced to 50 days in administrative detention [shortly after his arrest Hajiyev announced he was going on a hunger strike. According to media reports, he stopped the strike on December 29, 2022].
Another civil society member, Imran Aliyev was also kidnapped by the Main Department for Combatting Organized Crime where his devices and social media accounts were compromised against his will.
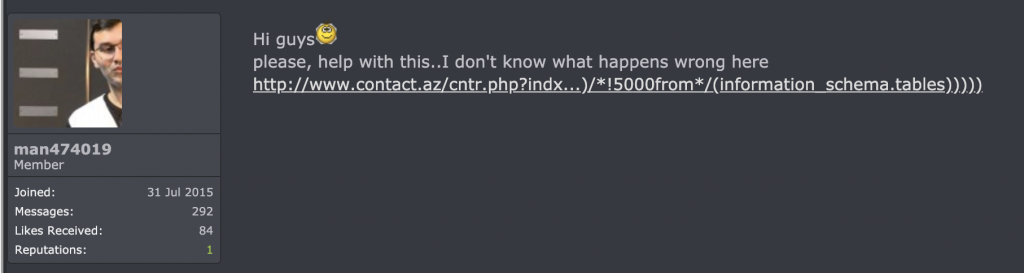
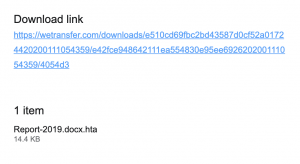
Abulfaz Gurbanli, also an active member of civil society, was phished through an email and WhatsApp messages in February 2022. A file disguised as grant-related information from a known donor organization containing a virus was sent to Gurbanli via his email. On WhatsApp, the activist received a message from someone impersonating herself as a BBC Azerbaijan Service journalist. The targeting resulted in the installation of spyware on his device and the hacking of his social media accounts.
At the time, Az-Net Watch requested assistance from Qurium media to analyze the link shared in the email and despite the journalist’s assurances, the link did contain a virus. “The mail pointed to a RAR compressed file in Google Drive that once downloaded required a password to be decrypted. The password to decrypt the file was included in the phishing e-mail: bbc. Compressed files that are password protected are common in malware phishing attacks as the files can not be scanned by antivirus,” concluded Qurium in its preliminary report. The further forensic report identified malware written in AutoIT. Once the link (in our case the link to a drive where the alleged journalist left questions for the political activist) was opened, the hacker through the deployed malware installed a persistent backdoor in the system. “The software connects to the domain name smartappsfoursix{.}xyz to download the rest of his software requirements. It downloads gpoupdater.exe and libcurl.dll which look responsible for uploading files to the command and control server. During the execution of the malware several (10) screenshots of the Desktop were uploaded to the server,” read the Qurium analysis.
Meanwhile, after taking over Gurbanli’s Facebook account, the hacker also deleted all of the content on at least seven of the community pages, where Gurbanli was an admin (screenshots below are from just two pages).
Az-Net Watch previously documented attacks through phishing emails sent to civil society activists last year. At the time, an email impersonating a donor organization was sent to a group of activists encouraging them to apply for a Pegasus Grant. Preliminary forensic results carried out at the time indicated that the malware sent around in this email was similar to a phishing campaign from 2017, that was widely covered and reported by Amnesty International: “The victims and targets identified, as well as the political theme of bait documents, indicate that the campaign is largely targeting human rights activists, journalists, and dissidents. This campaign also aligns with findings by VirtualRoad.org in their report, “News Media Websites Attacked from Governmental Infrastructure in Azerbaijan”, which links some of the same network address blocks with “break-in attempts” and “denial of service attacks” against several independent media websites. “The malware that was observed is not sophisticated and is in some manner extremely crude. However, combined with social engineering attempts and an unprepared public, these tactics can remain effective against many targets.”
In another case, an online media outlet – ToplumTV – social media accounts were hacked by intercepting incoming SMS, set up as a two-step authentication method. This resulted in the removal of countless news posts as well as subscribers to the channel’s social media account. The media outlet was previously targeted in September and November 2021 – in both instances, the social media accounts were hacked by SMS interception.
Feminist activists also witnessed a surge in online phishing attacks and hacking attempts ahead of the International Women’s Day protest scheduled to take place on March 8, 2022. At least three activists received support to ensure online safety during this period. Similar attacks and targeting were documented last year. In addition to compromised accounts, some feminist activists have faced account impersonation. Most recently, activist Narmin Shahmarzade reported to Az-Net Watch, that a fake Instagram account impersonating the activist shared Sharmazade’s photos in the absence of her consent with inappropriate captions. Az-Net Watch is currently working with the platform to remove the fake account.
Users of social media platforms, who posted critical of the government comments and posts, were also summoned to law- enforcement bodies where they were either forced to hand in their devices and passwords to their social media accounts or to delete their posts that were critical of the government. At least in 5 cases, activists and bloggers faced administrative arrests and interference with their social media accounts for their criticism online and activism.
One of the most recently documented cases includes a blogger who was called into questioning after sharing a video on Facebook of the traffic police accepting a bribe. The blogger was forced to remove the video after the questioning at the police station. Aziz told Meydan TV that police threatened to keep him less he removed the video. After Aziz told the local media about the pressure from the police, the blogger was called back into the questioning together with his parents.
In November, prominent lawyer, Elchin Sadigov said the law enforcement refused to return his mobile devices after the lawyer, would not share his passwords. Sadigov was arrested in September 2022 together with an editor of an independent outlet. In an interview with Meydan TV, Sadigov said, he considered demands that he shares his login credentials were a violation of privacy.
Also in November, a member of D18 political movement, Afiaddin Mammadov, who was arrested on bogus charges and sentenced to 30 days in administrative detention said he was tortured by the local police officers after refusing to share his password to his device.
Other documented instances of social media users targeted over their online criticism this year include:
- police briefly detain a member of an opposition party over social media posts/;
- questioning over social media posts critical of government measures raise concern/;
- police detains political activist over facebook posts/;
- two website editors and three social media users questioned over disseminating forbidden information on the internet/;
- several social media users warned one sentenced to 30 days of administrative-detention/;
In April, Meta released its pilot quarterly Adversarial Threat Report in which the platform said it identified “a hybrid network operated by the Ministry of the Internal Affairs.” According to the document, this network relied on, what Meta refers to as, “Coordinated Inauthentic Behavior [CIB]” in combination with cyber espionage, “compromising accounts and websites to post” on behalf of the Ministry. According to the report, these coordinated online cyberattacks targeted journalists, civil society activists, human rights defenders, and members of opposition parties and movements in Azerbaijan. The ministry’s press office was quick to dismiss the findings, saying the findings were fictitious.
Azerbaijan was also among countries identified in Pegasus leaks targeting some 80 government critics among one thousand other Azerbaijanis identified in the targeting with Pegasus spyware.
The attacks and support provided, in the course of the past year, illustrate that no matter how well-prepared political activists and members of civil society are in Azerbaijan, digital security awareness is insufficient in autocratic contexts like Azerbaijan.
We also observed that existing legal remedies in the country are insufficient to find perpetrators behind such targeting and hold them to account. While in a few instances targeted community members filed official complaints, the investigative authorities showed reluctance in effectively investigating the incidents.
This year, Az-Net Watch published this detailed report about litigating Pegasus in Azerbaijan in which together with a legal expert we conclude that existing national legislation concerning privacy and surveillance is insufficient, and is left to vague and often overt interpretation in the hands of law enforcement and prosecutor office. As such, Azerbaijan continues to systematically fail in providing effective legal remedies and sound investigations against state-sponsored digital attacks and surveillance. Moreover, despite evidence-based reports of targeted and coordinated cyber attacks against activists, the government thus far has not investigated and/or provided effective legal guarantees. And in all cases filed for investigations, nearly a year later after Pegasus spyware has been identified to be in use, the law enforcement authorities are yet to take formal investigative actions.
In another report published this year together with a legal expert, Az-Net Watch identified serious gaps in data privacy protection mechanisms in Azerbaijan. Our analysis indicated that the national legislation on personal data protection does not effectively protect individuals against the arbitrary use of their personal data by both public and private entities. The analysis also indicated that the national laws restrict and control personal data with intrusive measures, such as equipping telecom networks with special devices, and real-time access to vast amounts of personal data, in the absence of a criminal investigation or judicial order.
Conclusion
These and other instances of digital threats and offline persecution for online activism illustrate that internet freedom in Azerbaijan continues to decline with no signs of abating. For yet another year, Azerbaijan was ranked “not free” in Freedom on the Net 2022 report released by Freedom House. In addition to scores of news websites currently blocked in the country (a practice observed since 2017), the state has also resorted to blocking or throttling access to social media platforms and communication applications in recent years. In September 2022 the state demonstrated its control over the internet by blocking access to TikTok on the grounds the platform was casting a shadow over military activities, revealing military secrets, and forming wrong public opinion. The blocking was carried out amid renewed military tensions between Armenia and Azerbaijan. Other users said they experienced issues accessing WhatsApp, Telegram, and slow internet connectivity speeds. Previously, during the second Karabakh war (in 2020), users in Azerbaijan faced internet restrictions as well.
Civic activists in Azerbaijan express concern over state control of the internet at a time, when social media platforms, and independent as well as opposition online news sites have become the sole sources of alternative information accessible to the public outside of traditional media.
The present environment is further exacerbated by the continued crackdown on civic activists as in the case of Bakhtiyar Hajiyev mentioned earlier in the report. In addition, a number of critical bills approved by the parliament this year, demonstrate a profound lack of interest on behalf of the state to ensure basic freedoms including freedom of the media and of association. As of February 2022, a restrictive new media law compels online media outlets to register with the government agency and has imposed a number of other critical requirements and criteria that critics say only serve the purpose of silencing independent journalists and news platforms.
On December 16, 2022, the parliament also approved a critical bill on political parties, introducing a new set of exhaustive restrictions on political parties.
As such, Azerbaijani civil society is facing a turbulent year ahead both offline and online in an environment dominated by state control on all forms of dissent leaving many wondering how far the state is willing to go to silence the critics.

![Hacks and compromised accounts continue to target journalists and activists in Azerbaijan [updated September 13]](https://www.az-netwatch.org/wp-content/uploads/2020/09/markus-spiske-qjnAnF0jIGk-unsplash-600x400.jpg)






![mass phishing attack against Azerbaijan civil society [updated]](https://www.az-netwatch.org/wp-content/uploads/2019/12/computer-security-or-safety-concept-laptop-PQ7RZZ5-533x400.jpg)