It’s been months since an investigation led by an international consortium of journalists and technology experts revealed how Pegasus, a hacking software developed and sold by an Israeli surveillance company, NSO group targeted civil society representatives globally. On the country lists of phone numbers identified to have been targeted with Pegasus were numbers that belonged to dozens of civil society activists in Azerbaijan. Abulfaz Gurbanli, a political activist, was among them.
After learning that his device was infected, Gurbanli wiped his entire device and had it reset. On February 15 after plugging his device into a power adapter, Gurbanli’s device was remotely reset. Shortly after, he lost access to his Gmail account. The reset got rid of the google authenticator Gurbanli had set up to access his email account. Within hours, the political activist also lost access to his Facebook profile. Although the URL was briefly inaccessible on Facebook, it has been reinstated. Gurbanli finally secured access to his account on February 17.
In addition to a remote reset, Gurbanli also had multiple attempts to hack into his Facebook and Telegram accounts earlier. AIW spoke with a digital security expert who took a closer look at the IP address where these attempts originated from, indicating that it was the same IP that targeted other activists in the past few months.
There is suspicion that Gurbanli’s device was re-infected with Pegasus. But these suspicions can only be confirmed after a thorough device forensic analysis.
Fake interview request
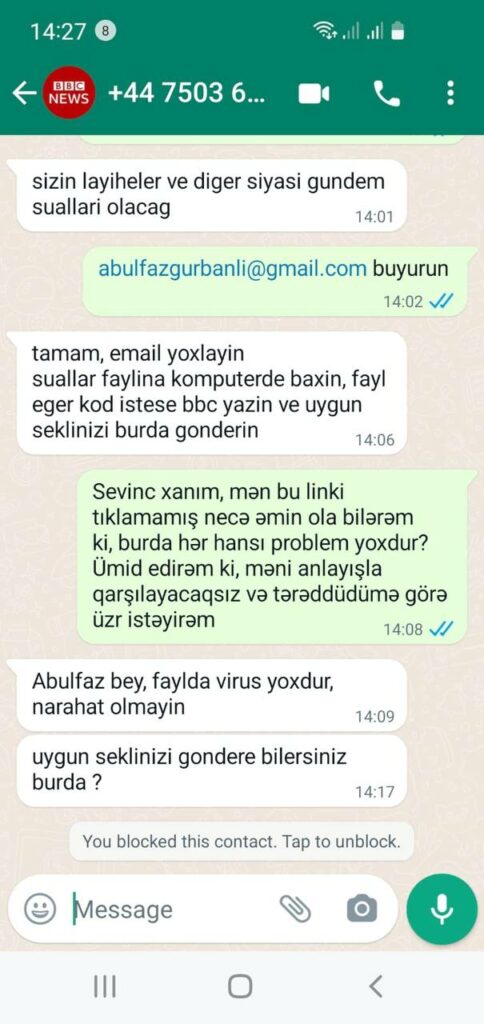
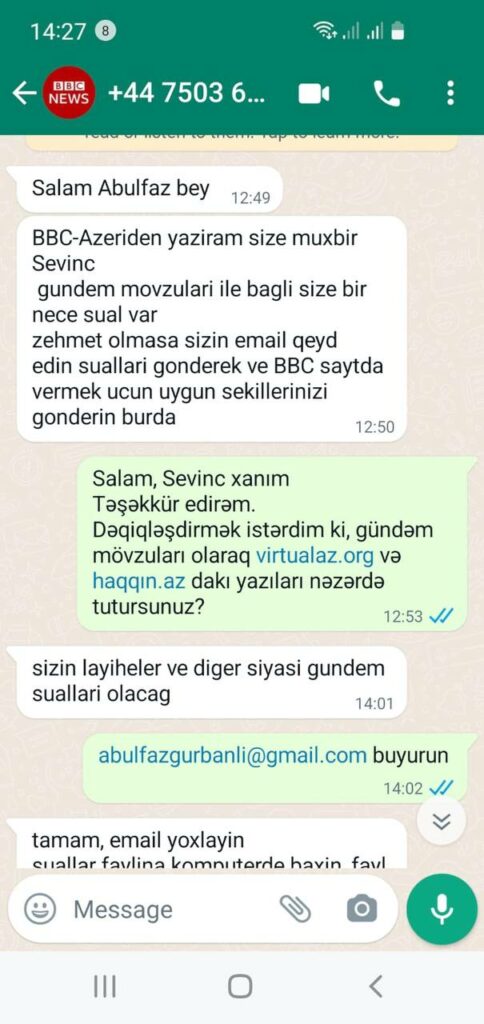
On February 15, Gurbanli received an email from BBC Azerbaijan Service asking him for an interview.
The journalist, who introduced herself as Sevinc, also contacted Gurbanli via WhatsApp.
Translation:
Sevinc: Hello Mr. Abulfaz. Writing to you from BBC Azerbaijan service, journalist Sevinc. I have a few questions about the agenda topics. Can you please share your email address and send us suitable pictures for the BBC website?
Gurbanli: Hello Ms. Sevinc. Thank you. I wanted to clarify whether you are referring to stories published on virtualaz.org and haqqin.az when you refer to the agenda topics?
Sevinc: It is about your projects and other political agenda.
Gurbanli: [sends his email address]
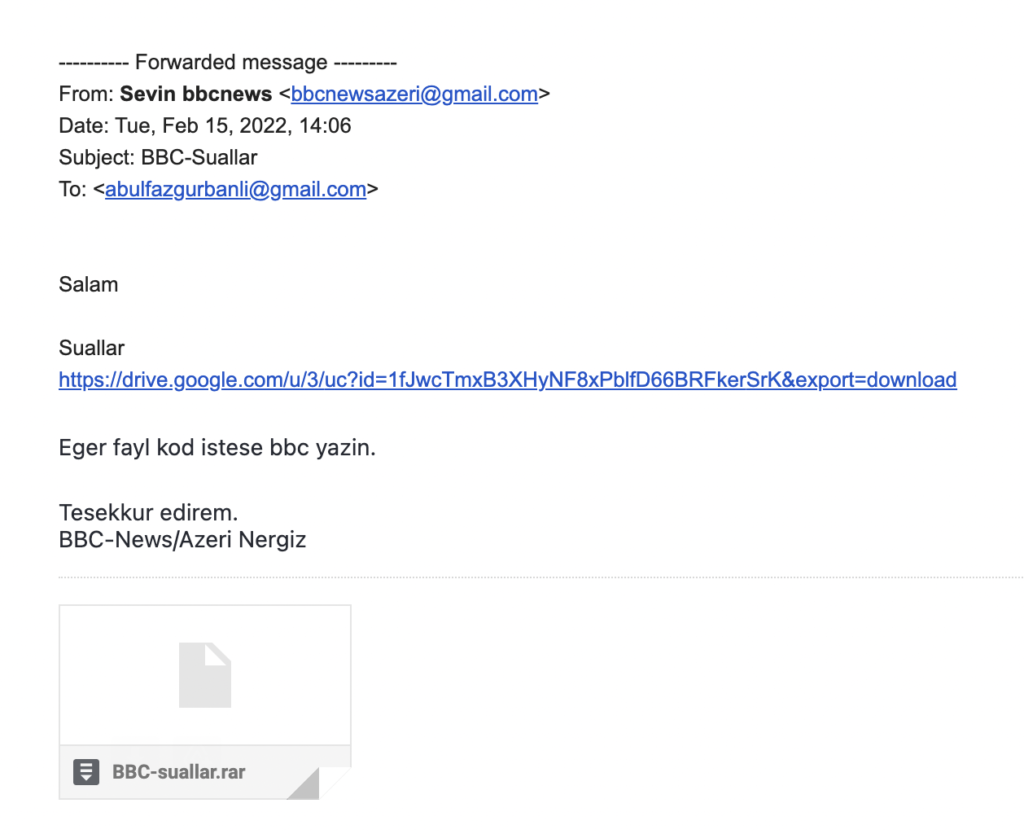
Sevinc: ok, check your email, there is a file with questions you can check on your computer. If the file requests a code, just write bbc and send us a suitable picture.
Gurbanli: Ms. Sevinc how do I know the link you have sent does not have a virus. I hope you understand this and I apologize for hesitating.
Sevinc: Mr. Abulfaz, the file does not contain virus, don’t worry. Can you please send a picture?
AzNet Watch has written to azeri@bbc.co.uk – the official email address of the Azerbaijan service informing the service of the incident.
AzNet Watch also requested assistance from Qurium media to analyze the link shared in the email and despite the journalist’s assurances, the link did contain a virus. “The mail pointed to a RAR compressed file in Google Drive that once downloaded required a password to be decrypted. The password to decrypt the file was included in the phishing e-mail: bbc. Compressed files that are password protected are common in malware phishing attacks as the files can not be scanned by antivirus,” concluded Qurium in its preliminary report. Further forensics report identified malware written in AutoIT. Once the link (in our case the link to a drive where the alleged journalist left questions for the political activist) was opened, the hacker through the deployed malware installed a persistent backdoor in the system. “The software connects to the domain name smartappsfoursix{.}xyz to download the rest of his software requirements. It downloads gpoupdater.exe and libcurl.dll that look responsible for uploading files to the command and control server. During the execution of the malware several (10) screenshots of the Desktop were uploaded to the server,” reads the Qurium analysis.
Meanwhile, after taking over Gurbanli’s Facebook account, the hacker also deleted all of the content on at least seven of the community pages, where Gurbanli was an admin (screenshots below are from just two pages).
These attacks came shortly after a pro-government media published an article targeting Gurbanli accusing the political activist of allegedly organizing color revolutions in Azerbaijan.
![Deliberate targeting in pro government media leads to targeted attacks online – the case of Abulfaz Gurbanli [Updated]](https://www.az-netwatch.org/wp-content/uploads/2022/02/malware-600x300.jpeg)