Between May 13 through 17, four different video clips from private Zoom calls were leaked online. The videos were taken from calls that took place between senior members of the National Council of Democratic Forces (NCDF), an alliance representing several opposition parties in Azerbaijan. The members of the council called the leak a cybercrime committed on behalf of the ruling government. Some have called on the authorities to investigate as this is a breach of privacy according to national legislation, while others, claimed authorities were using NSO Group’s Pegasus spyware.
Until now, no clear evidence emerged indicating that indeed, Pegasus is being used in Azerbaijan. And while AIW continues its investigation into the recent leak, here is a detailed look at other available surveillance and disruption technology the government of Azerbaijan has purchased over the recent years that have the potential of eavesdropping on users’ devices. That, combined with the recent numerous reports about the Zoom app’s security vulnerabilities may provide at least some answers.
What spyware technology Azerbaijan has purchased until now
The interest in snooping on Azerbaijani nationals is not something new for a country that has been criticized by international human rights watchdogs for years over its poor record on human rights and freedoms.
In 2012, an investigative documentary film revealed how companies owned by Teliasonera [namely Azercell in Azerbaijan at the time] “allowed for “black box” probes to be fitted with their telecommunication networks. These boxes allowed for security services and police to monitor in real-time and without any judicial oversight all communication passing through, including texts, internet traffic, and phone calls.”
Two years later, Azerbaijan investigative journalist Khadija Ismayilova revealed that the country’s largest telco had ties to the ruling family, namely to the two daughters of President Ilham Aliyev, raising questions about Internet surveillance and communications security.
The same year, Citizen Lab, identified Azerbaijan, among potential customers of Milan based Hacking Team that sold surveillance equipment called Remote Control System (RCS) to Azerbaijan as well as many other countries whose rights and freedoms record been marred with violations.
“The capabilities of its flagship product, the Remote Control System (RCS), include extracting files from a targeted device, intercepting emails and instant messaging, as well as remotely activating a device’s webcam and microphone.”
Source: New traces of Hacking Team in the wild
Among significant features of RCS are:
- capture data that is stored on a target’s computer, even if the target never sends the information over the Internet;
-
enable government surveillance of a target’s encrypted internet communications, even when the target is connected to a network that the government cannot wiretap;
-
copy files from a computer’s hard disk, record skype calls, e-mails, instant messages, and passwords typed into a web browser;
-
turn on a device’s webcam and microphone to spy on the target
Moreover, the same CitizenLab report identified an active endpoint in Azerbaijan that was active between June and November 2013 – the year, when Azerbaijan had its presidential election [October] and accidentally announced the results of the election over an app before the voting even began.
In 2015, Organized Crime and Corruption Reporting Project (OCCRP) confirmed that the Azerbaijan government was indeed a customer of the Hacking Team. Pointing at records showing the country’s Ministry of Defense among the company’s clients.
Also in 2015, the Azerbaijan government expressed interest in purchasing Dataminr technology for its ability to “explore an individual’s past digital activity on social media and discover an individual’s interconnectivity and interactions with others on social media.”
| The company’s 2015 marketing material, […] suggests that identifying individual users was a key part of Dataminr’s pitch to foreign governments by allowing users to quickly locate the “original source” behind a breaking news alert, and then find that person’s most popular tweets, what hashtags they have used in the past, and who has shared their tweets. |
AIW reached out to Dataminr to confirm whether the transaction took place and received the following response:
“We currently do not have any relationship with the Government of Azerbaijan nor do we intend to do so in the future.”
The same year, the government purchased specialized security equipment – Deep Packet Inspection (DPI) to be used to monitor and block social media during the first European Games, Baku was hosting. The equipment was purchased for 3millionUSD from an Israeli company Allot Communications.
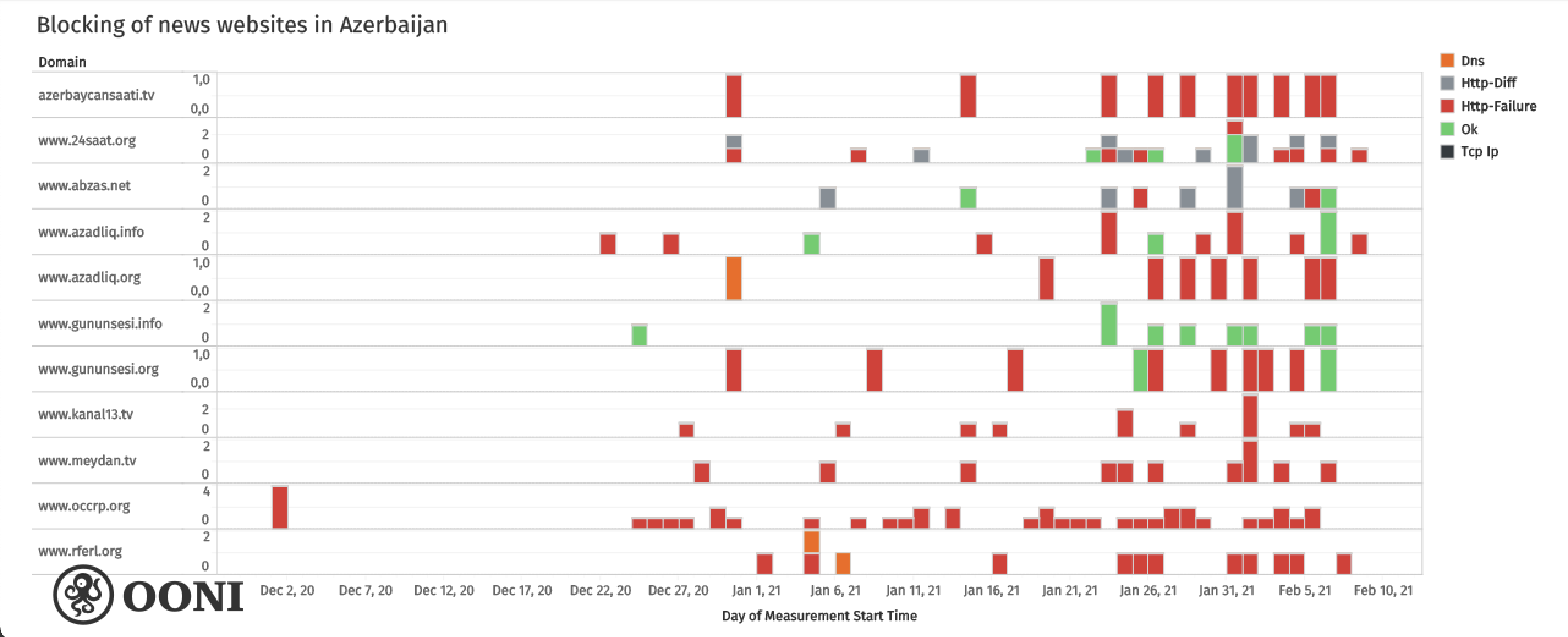
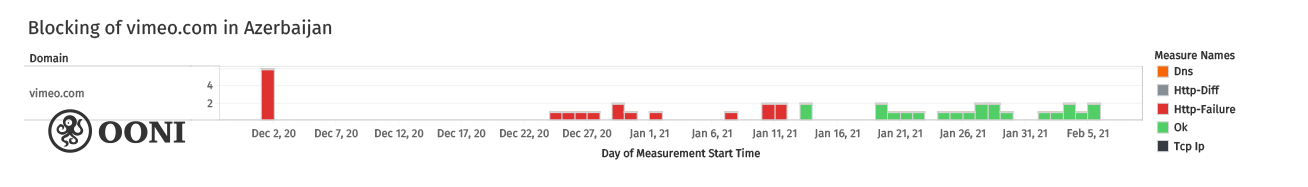
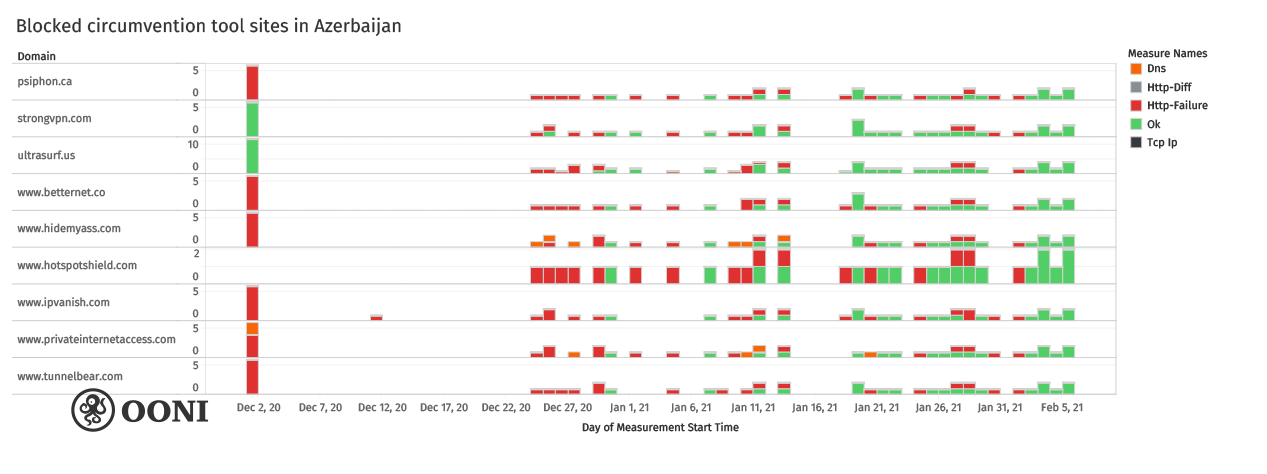
In 2016 before access to independent online news platforms is blocked, evidence shows, how the government was behind generating artificial internet network congestion within Azerbaijan to prevent access to RFERL Azerbaijan Service; VoA; and Meydan TV. The same year, first mass, spear-phishing attack targets prominent rights defender and former political prisoner Rasul Jafar.
In March 2017, the same DPI technology that purchased in 2015, is used to block some of the main independent media platforms in the country.
Also in 2017, Azerbaijan purchased another Israeli surveillance product, Verint Systems which was used in targeting of LGBTW+ on Facebook.
“I was training [clients on the use of Verint software] in Azerbaijan,” related Tal. “One day, the pupils came to me during a break and asked how they could [use the software to] determine someone’s sexual preference on Facebook. It was only later, when I read about the issue, that I discovered the country is notorious for persecuting the [LGBT] community. Suddenly things came together,” said one former Verint employee in an interview.
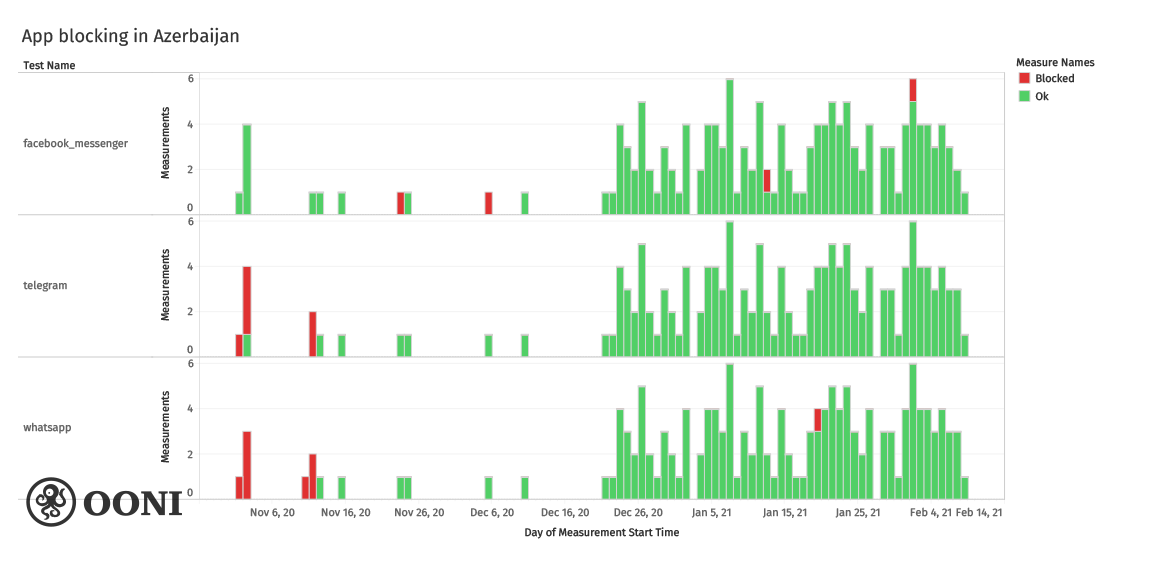
In general, the volume of digital attacks on representatives of civil society in Azerbaijan has been on the rise in recent years and especially since 2018. This was also highlighted in 2018 by Access Now, Digital Security Helpline. Many of these and other cases were covered here and here.
Meanwhile, AIW also looked into the possibility of Pegasus software being used in Azerbaijan following the claims made by some of the civil society representatives in the country. So far, AIW found no evidence for this to be the case. However, there is plenty of other technology available that can help the ruling government to eavesdrop and snoop around.
Taking into account Zoom vulnerabilities
Over the recent months, a number of reports on Zoom’s security vulnerabilities have also made it clear, that without E2E (end to end corruption) and with several other security-related shortcomings, Zoom does not offer, fully secure communication platform and that potential loopholes within the program may have made the leak reported in Azerbaijan possible.
- according to researchers at Morphisec Labs there is a Zoom app bug that can enable malicious actors to record Zoom sessions and capture chat text without any of the meeting participants’ knowledge. The malware also prevents any users in a meeting from being made aware of the recording;
- malicious actors can assume control of a Zoom user’s microphone or webcam;
- Zoom could be compelled to hand over data to governments that want to monitor online assembly or control the spread of information as activists move protests online;
The last point, is especially important, as unlike companies like Google, Facebook an Twitter, Zoom is yet to release information about whether there have been cases of government requests for data it gets, and how many of those requests it complies with. The company was encouraged to do so following an open letter and Zoom promised to publish a transparency report.
Back to Azerbaijan
Taking into account the history of surveillance and equipment purchased by government vendors over the last decade, the consistent crackdown against activists during COVID, it is likely that combined with Zoom’s security vulnerabilities, the leaked video calls were recorded by a third actor, and later leaked online for the purpose of sowing discord among opposition groups.