Account compromise, website hacks, DDoS attempts, phishing are just a handful of tactics used to target journalists, rights defenders, and activists in Azerbaijan.
Here is a list of new cases:
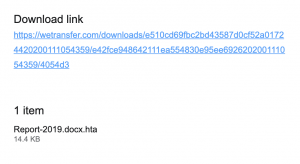
Earlier in July, Azerbaijan Internet Watch reported a phishing attack that targeted some of the civil society activists. Following a forensic investigation carried out in partnership with Qurium, it was possible to confirm that the email was indeed a virus. According to preliminary conclusions, “the e-mail included a link to malware, with the capability of webcam and Desktop recording, execution of windows commands (WMI) as well as extraction and uploading of selected files from the victim’s computer.
Then the civil society was targeted with another phishing, this time the sender pretended to be the National Endowment for Democracy inviting recipients of the email to apply for a Pegasus Grant.
Preliminary forensic results indicated that the malware sent around in this email was similar to a phishing campaign from 2017, that was widely covered and reported by Amnesty International:
The victims and targets identified, as well as the political theme of bait documents, indicate that the campaign is largely targeting human rights activists, journalists, and dissidents. This campaign also aligns with findings by VirtualRoad.org in their report, “News Media Websites Attacked from Governmental Infrastructure in Azerbaijan”, which links some of the same network address blocks with “break-in attempts” and “denial of service attacks” against several independent media websites
The malware that was observed is not sophisticated, and is in some manner extremely crude. However, combined with social engineering attempts and an unprepared public, these tactics can remain effective against many targets.
The same month, Azerbaijan Internet Watch received confirmation that the former political prisoner, Tofig Yagublu’s Facebook profile was subject to numerous hacking attempts.
In early August, former leader of the opposition Musavat party, Isa Gambar reported that all of his social media accounts were compromised including his Facebook profile, Facebook page, and Instagram account.
On August 27, the website for popular platform HamamTimes was hacked. The team behind the platform, reported all of its content removed, suspecting that the hackers used the site’s vulnerability as a result of weak security protocols in place. So far, HamamTimes, managed to restore all of the website’s archive of stories however its hosting remains vulnerable to new targeting.
HamamTimes was targeted before as reported by Azerbaijan Internet Watch in a mass phishing attack.
On September 4, editor of anews.az news website, Naila Balayeva, reported that her Facebook account was compromised. The hacker switched the email account and the phone number originally registered for the profile. Although Balayeva was able to restore access to her email and change the emails, according to the journalist, the hacker continues to use Facebook as the owner often deleting posts that are critical either of the police or the government institutions.
Anews.az and Balayeva were targeted before. Last year, several Facebook pages affiliated with the website were hacked.
While it was possible to provide assistance in some of the cases, the response from platforms like Facebook, especially in the case of Gambar has been slow and at times, comical. So far, twice, the platform requested new emails not associated with the platform or any of its apps and twice, Gambar sent proof of identity.
[Update] On September 9, political activist Bakhtiyar Hajiyev was reportedly threatened by Baku Police Chief Alekper Ismayilov over a Facebook post, that Hajiyev wrote the same day. The post, Hajiyev wrote on Facebook was addressing the Ministry of the Interior, specifically the Minister of the Interior, Vilayat Eyvazov. The activist alleged the ministry was delaying a response to his complaint submitted 50 days ago over a street hooligan.
[From Hajiyev’s post on Facebook published on September 9, 2021] Instead of investigating why my Ministry of the Interior cannot question street hooligan, who is refusing to speak to them, humiliating police officers who show up at [the hooligan’s] home, Vilayat Eyvazov is going after me for reminding [the Ministry] of my complaint and is threatening me with arrest, death and blackmailing.
The activist told Turan News Agency that he was summoned to the police on September 9 where Baku Police Chief, Alekper Ismayilov allegedly told Hajiyev less he removes the Facebook post, the activist would face a greater punishment than arrest.
On September 12, Gubad Ibadoglu, Azerbaijani academic, and an economist reported that his Facebook profile and page were compromised. In an interview with Turan News Agency, Ibadoglu said despite his attempts to strengthen the security of his accounts, they were compromised anyway. “I got a message this morning that my password was changed using my own computer. This means that the hackers of the Azerbaijani government, even in London,” Ibadoglu told Turan. The fact that he received a notification informing him that his computer was the device from which the passwords were changed, means the device was infected with a virus containing some form of keylogger. It won’t be the first time, this type of information extraction is used to target Azerbaijani civil society.
[Update] In September, online news platform Toplum TV, reported it lost 16k followers on its Facebook page.
![Hacks and compromised accounts continue to target journalists and activists in Azerbaijan [updated September 13]](https://www.az-netwatch.org/wp-content/uploads/2020/09/markus-spiske-qjnAnF0jIGk-unsplash-600x400.jpg)


![inauthentic pages target independent news platform – will Facebook take notice [part 2, the case of Mikroskop Media]](https://www.az-netwatch.org/wp-content/uploads/2020/03/kon-karampelas-HUBofEFQ6CA-unsplash-600x400.jpg)


![mass phishing attack against Azerbaijan civil society [updated]](https://www.az-netwatch.org/wp-content/uploads/2019/12/computer-security-or-safety-concept-laptop-PQ7RZZ5-533x400.jpg)